-
NACTF - Sep 2019
Web
Pink Panther - 50
Rahul loves the Pink Panther. He even made this website: http://pinkpanther.web.2019.nactf.com
I think he hid a message somewhere on the webpage, but I don't know where... can you INSPECT and find the message?
Solution
Open the given link and view-source of the website
Scooby Doo - 100
Kira loves to watch Scooby Doo so much that she made a website about it! She also added a clicker game which looks impossible.
Can you use your inspector skills from Pink Panther to reveal the flag?
http://scoobydoo.web.2019.nactf.com
Solution
Open the given link view-source
To get flag, we need to change the opacity of <img> tags to 1
Dexter's Lab - 125
Please check in on your brother's lab at https://dexterslab.web.2019.nactf.com We know his username is Dexter,
but we don't know his password! Maybe you can use a SQL injection? Mom + Dad
Solution
Open the given link
To get flag, we need to login to the site with username dexter and password
1' OR '1'='1a basic SQL Injection
Sasame street - 150
Surprisingly, The20thDuck loves cookies! He also has no idea how to use php.
He accidentally messed up a cookie so it's only available on the countdown page... Also why use cookies in the first place?
http://sesamestreet.web.2019.nactf.com/
Solution
Open the given link
Go to http://sesamestreet.web.2019.nactf.com/countdown.php. Edit cookie session-time,
change the Path to flag.php, change the value to a large number such as 2568986265.
Finally, go to http://sesamestreet.web.2019.nactf.com/flag.php, we will get flag
spoilers
NACTF 2019 Newbie CTF 2019 RITSEC CTF 2019 UTC CTF 2019 KAF CTF 2019
-
Newbie CTF - Nov 2019
Forensics
Top Secret - 643
He stole the virtual machine file containing the top secret of the enemy country.
However, due to the shortage of USB memory, I dumped only the memory that seemed to be the most important.
What is the secret of an enemy country? (Fake Flag file exists.)
https://drive.google.com/file/d/1eQMKWR8y-c2zPzqZFmncj0h8S7advhSm/view?usp=sharing
Solution
Download the given File
The file is VMEM which is a virtual memory (RAM of virtual device)
To analyse VMEM files, we can use Volatility tool with this Reference
But we can also solve this task by simply finding strings since we know the flag format
strings "Windows 7 Enterprise K-b94208dd.vmem" | grep -oE "KorNewbie{.*}"
Chat - 980
Confidential information came and went through chat. Find the email of the user who used the chat.
Flag: KorNewbie{email_address}
https://drive.google.com/open?id=1Gfz5e-rwDSz14MWPfhGBfKHqfAjPGVXX
Solution
Download the given File
The file contains Windows 10 Virtual Machine which can be imported to VMware or Virtual Box
Since no password has been provided for windows 10 virtual machines, we have to bypass the windows password
After bypassing windows password goto recent files in This PC. we find a Document named "last_pc_login.dat"
Open the file "last_pc_login.dat" and you will find the required email addresss
-
RITSEC CTF - Nov 2019
Web
Misdirection - 100
Looks like someone gave you the wrong directions!
http://ctfchallenges.ritsec.club:5000/
Flag format is RS{ }
Solution
Open the given Link in Burp proxy
We can observe the page redirects several times
Analyse the pages at Burp - Proxy - HTTP History, we can see the redirected pages have single charaters R, S, %7B, 4, etc. which is in our RI{} flag format

Buckets of Fun - 100
http://bucketsoffun-ctf.s3-website-us-east-1.amazonaws.com/
Solution
Open the given Link
It’s clear that the challenge has something to do with aws s3 buckets as per challage name & URL
May be the aws bucket has flag file
Open the base aws s3 link at http://bucketsoffun-ctf.s3.amazonaws.com/
Here we can observe the following source code
bucketsoffun-ctf
1000
false
index.html
2019-11-18T14:05:20.000Z
"b271e7783d480770f61670d6b234e1ed"
630
STANDARD
youfoundme-asd897kjm.txt
2019-11-18T14:05:20.000Z
"a920cc3c8aaa05c1afe96a78d0adbcda"
25
STANDARD
There is a file youfoundme-asd897kjm.txt which has required flag
-
UTC CTF - Dec 2019
Misc
ezip - 31
Given two files flag.zip and cat.png
Solution
Analyse both the file
flag.zip is password protected and we need to crack the password by using tools such as fcrackzip
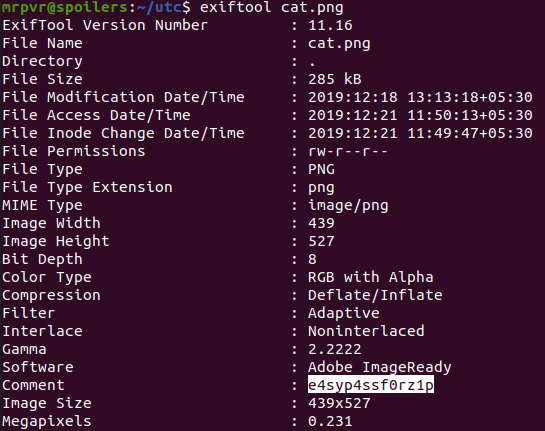
But we have another file cat.png, by analyzing this image using exiftool we can find flag.zip's password
Use the password to unzip the flag.zip and we get flag.txt which contains our required flag
Optics 1 - 42
Given an image Challange1.png but there is an error opening the image
Solution
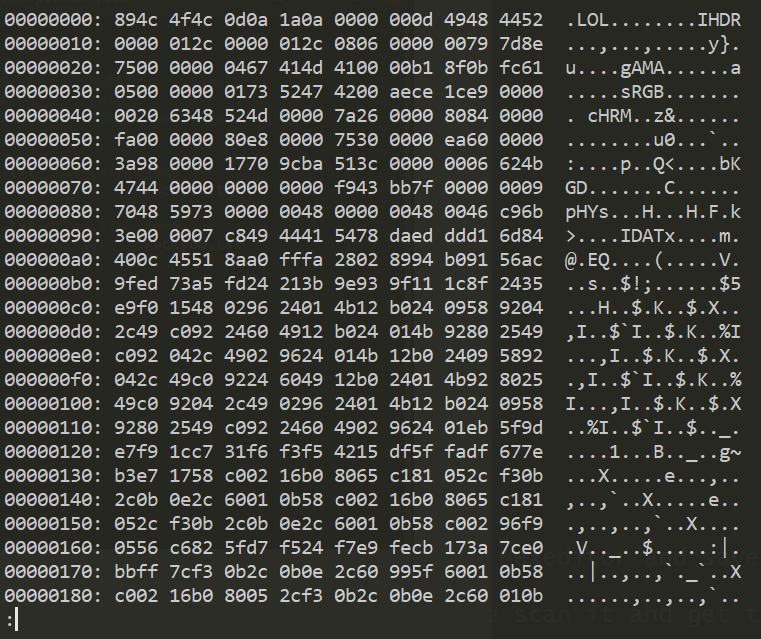
Analyse the image header using XXD in linux or any other Hexeditor
The png header is .PNG but here it is .LOL
Edit and change the .LOL header to .PNG by using Hexeditor and save the image
Now try to open the saved images we get a QR code scan it and get the flag
Reverse Engineering ♥
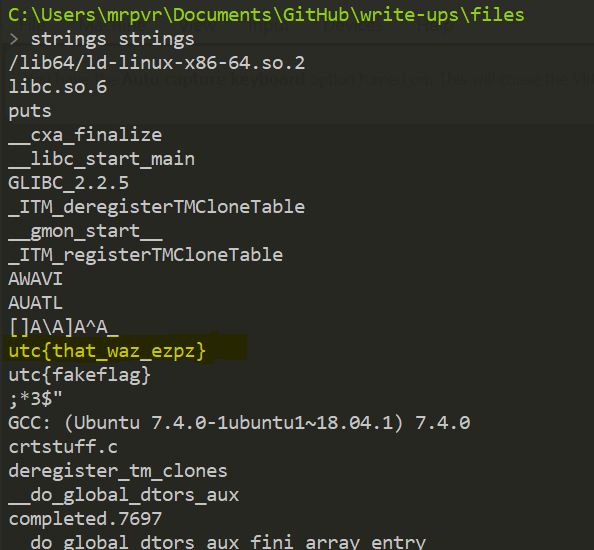
Strings - 26
The strings file is an ELF executable
Solution
Since the title of the challange says Strings
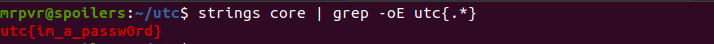
Search for strings using strings command
Note: There is also a fake flag
utc{fakeflag}
Corey's core dump 1 - 35
The core file is an ELF executable
Solution
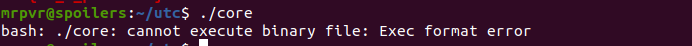
First things first, always try to find and understand the executable file
Here the ELF file cannot run
Lets run strings same as previous challange
Strings is a saviour
Jump - 70
The jump file is an ELF executable
Solution
Level up, no strings this time
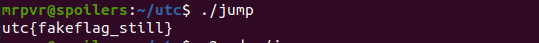
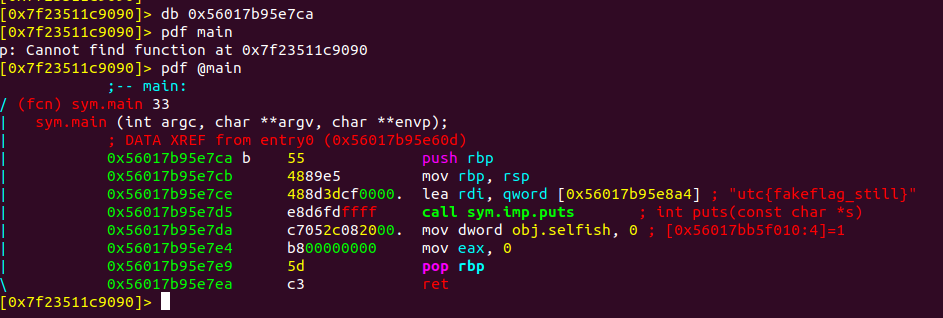
Run the file we get a fake flag
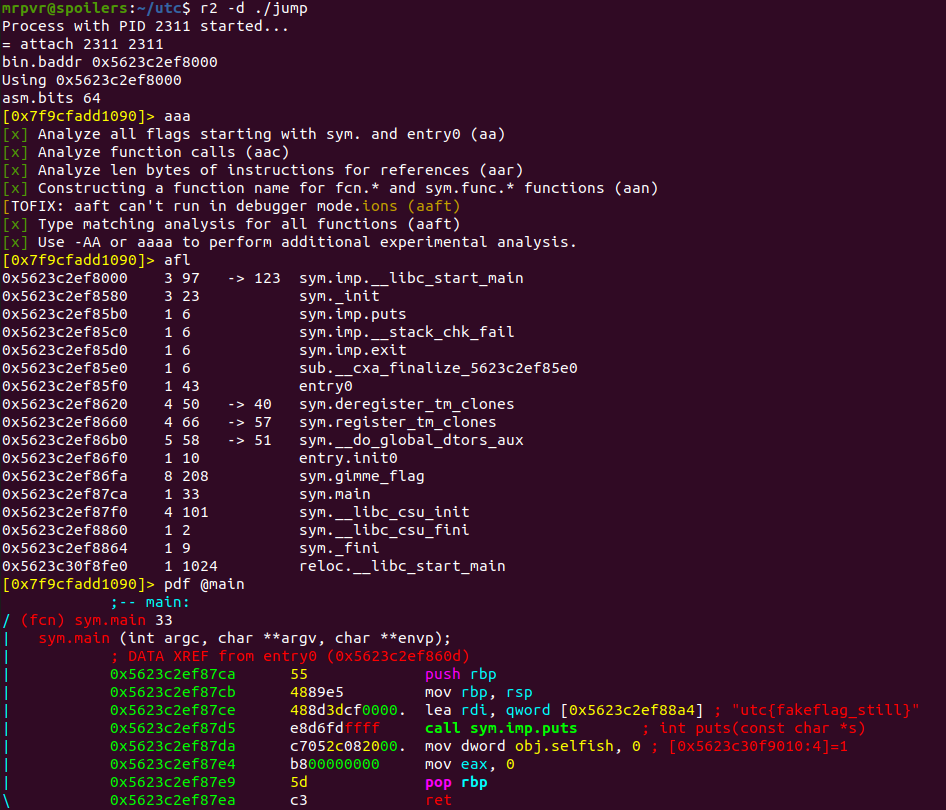
Lets start analysing the file using radare2
There is a function called sym.gimme_flag but that function is not included in the main function
So we have to make a jump to that sym.gimme_flag function to obtain the flag
Let's start by setting a break point at starting of main
Now Seek to sym.gimme_flag function
Run the binary using dc command it hits the break point at main
Now jump to function sym.gimme_flag using command dr rip=0x55680b9936fa (Starting address of sym.gimme_flag function)
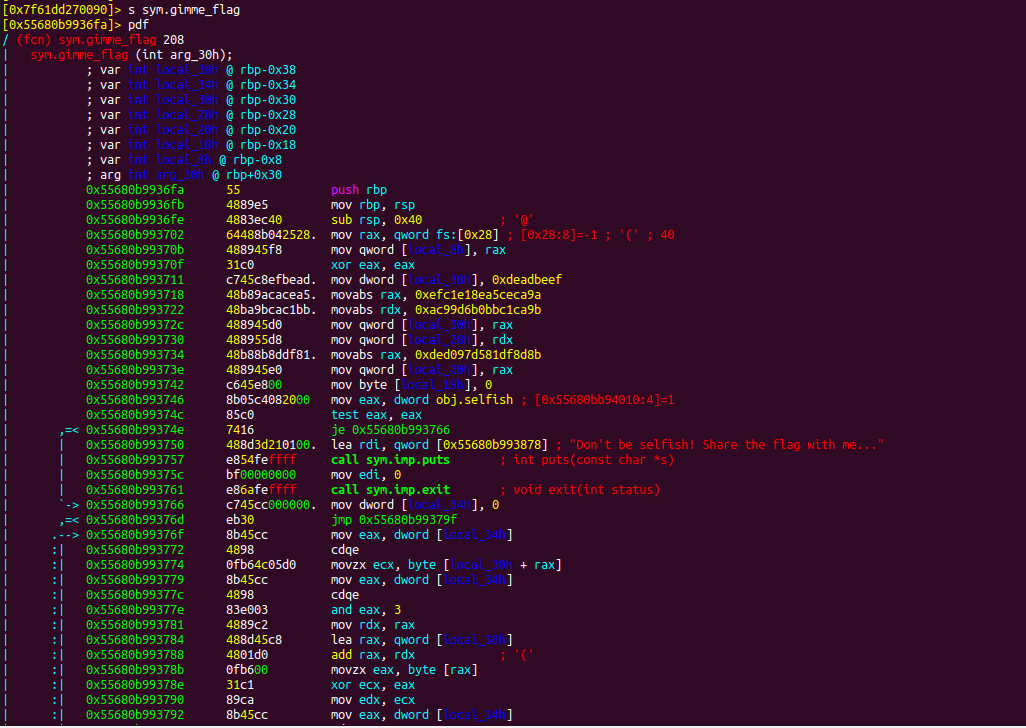
If we analyse carefully there is another jump to make inorder to get the flag
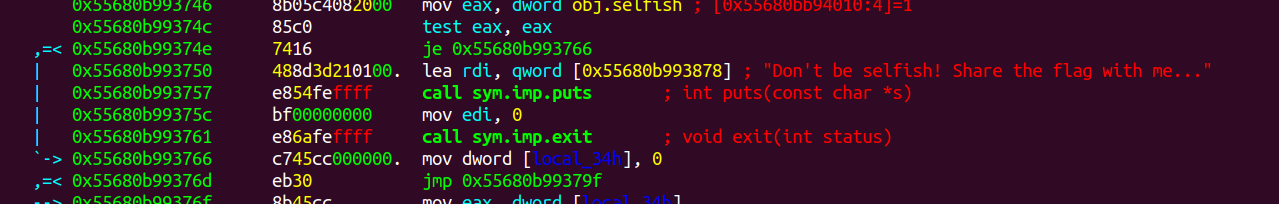
In sym.gimme_flag function there is je 0x55680b993766 which doesnot take the jump
So set another break point at je 0x55680b993766 which as address 0x55680b99374e
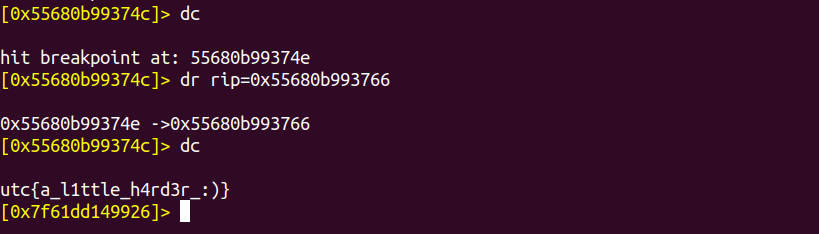
Run the binary again using dc it hits the break point again, now jump to 0x55680b993766 address using command dr rip=0x55680b993766
Again run dc to get the flag
-
Kipod After Free CTF - Dec 2019
Web
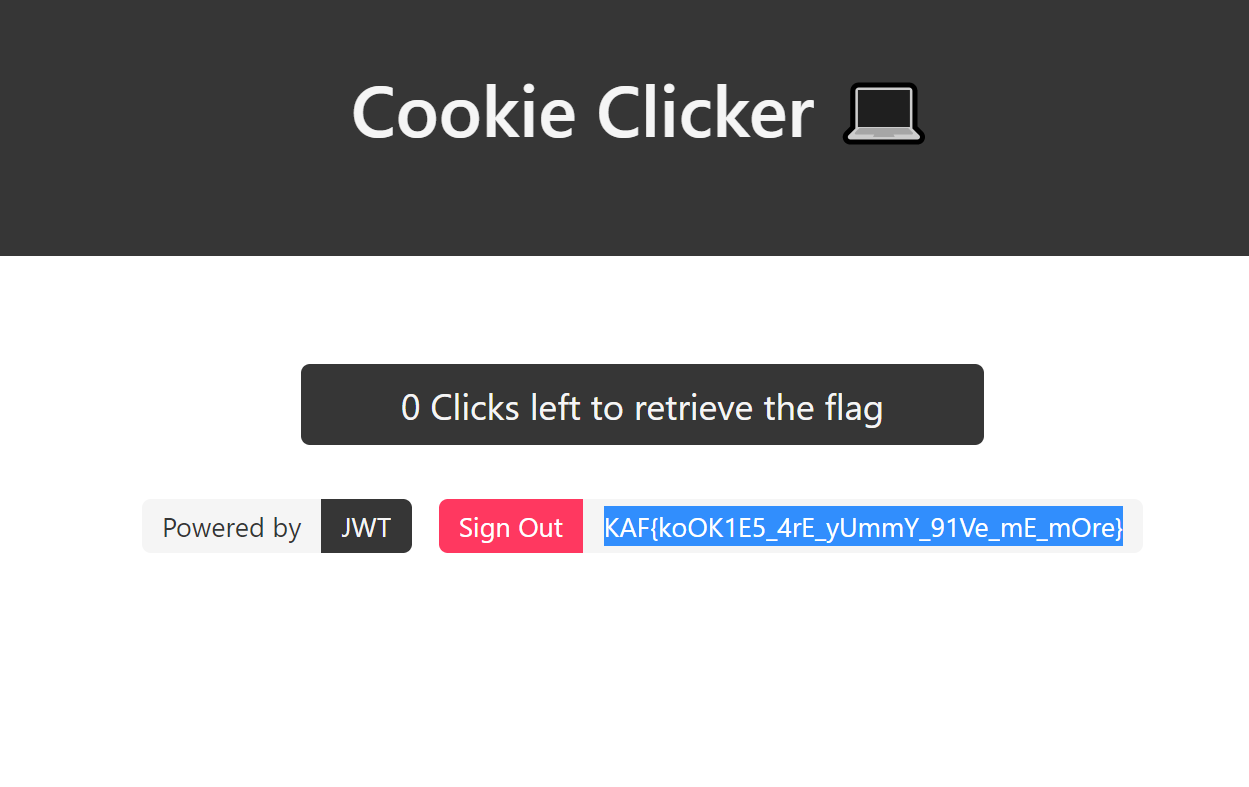
Cookie Clicker - 25
Solution
Go to the given link and sign in with a username
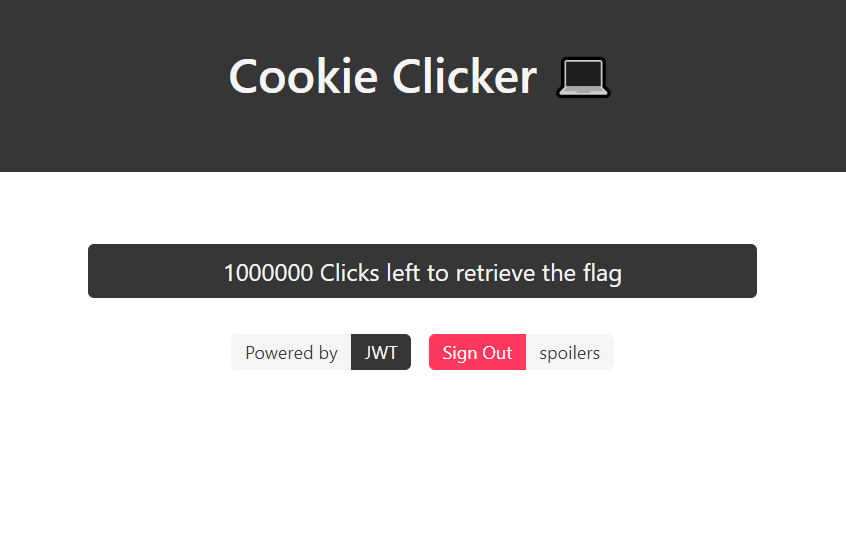
If we click
1000000times we get the flag; LOLChallange Tags: Cookie, JWT, rock says we have to crack the JWT cookie using rockyou.txt as wordlist
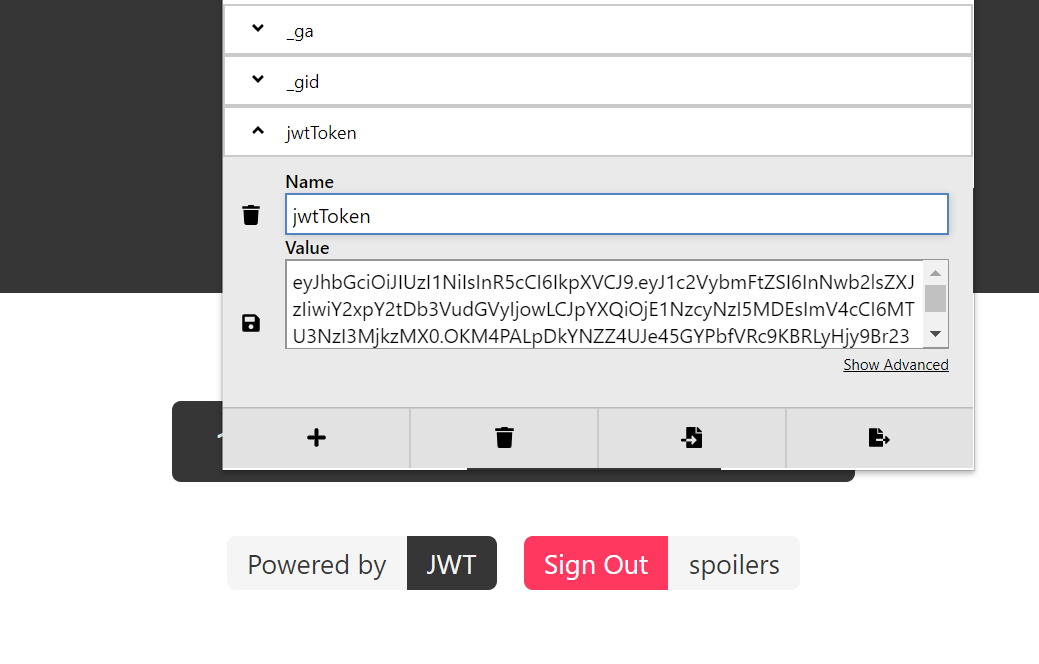
Copy the cookie from browser
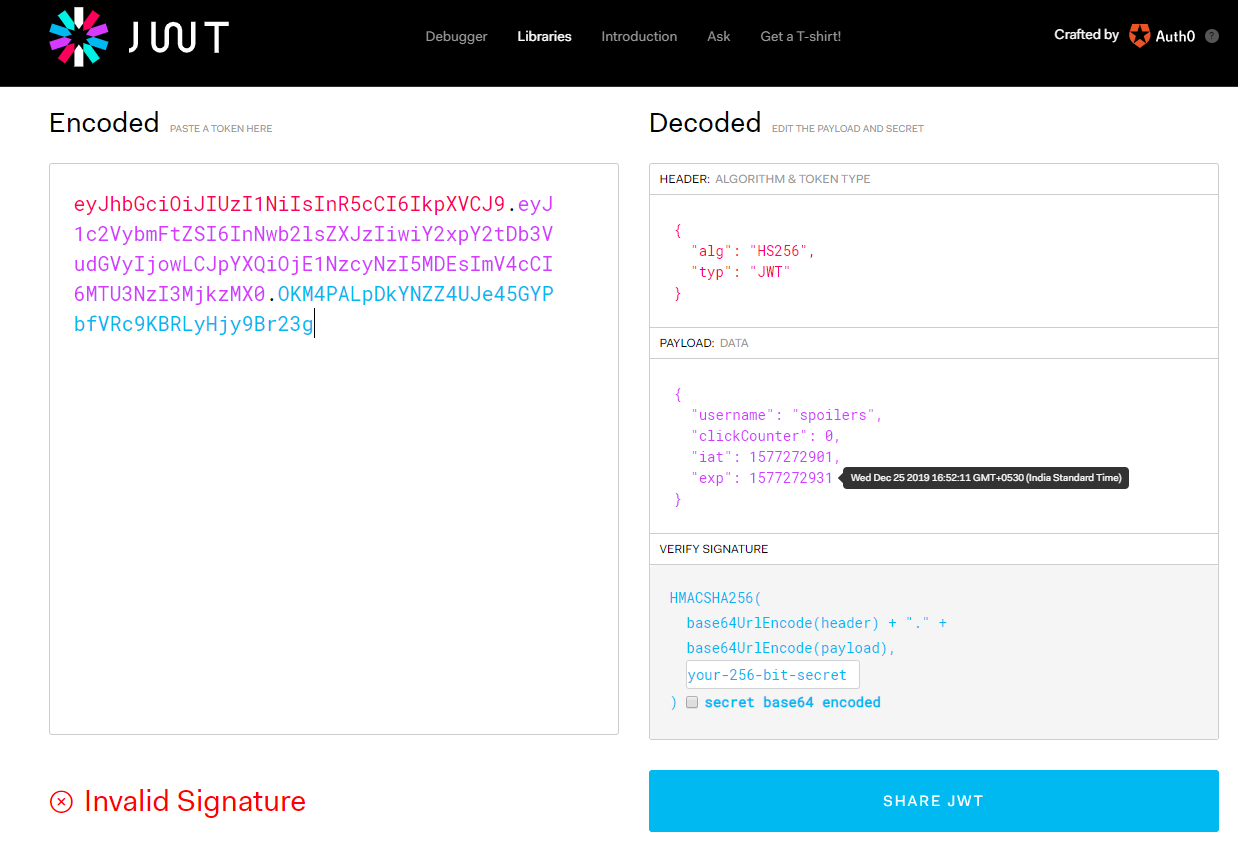
Go to www.jwt.io debugger and analyse the JWT cookie
To obtain flag we have to change the "clickCounter" value from "0" to "1000000", to do this we have to first crack the JWT secret key to get valid JWT signature
We can crack JWT secret key using John the Ripper, but first we have to convert JWT to a valid John the Ripper hash
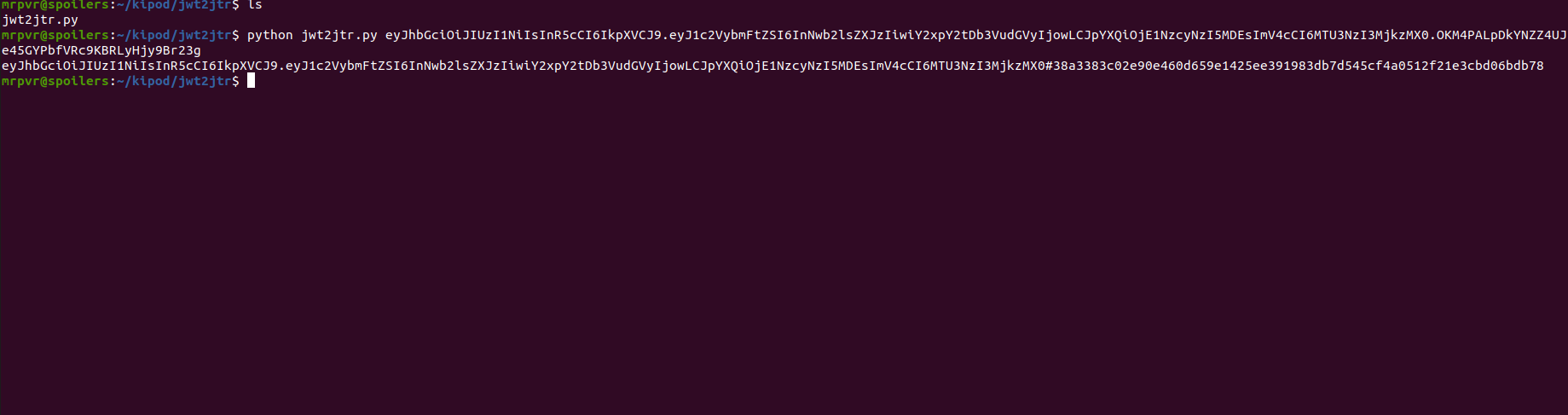
Go to link download the file jwt2jtr.py
Using command python jwt2jtr.py eyJhbGciOiJIUzI1NiIsInR5cCI6I...........Z6Rttqj40k6oeGrPVXm0 convert JWT to John the Ripper hash
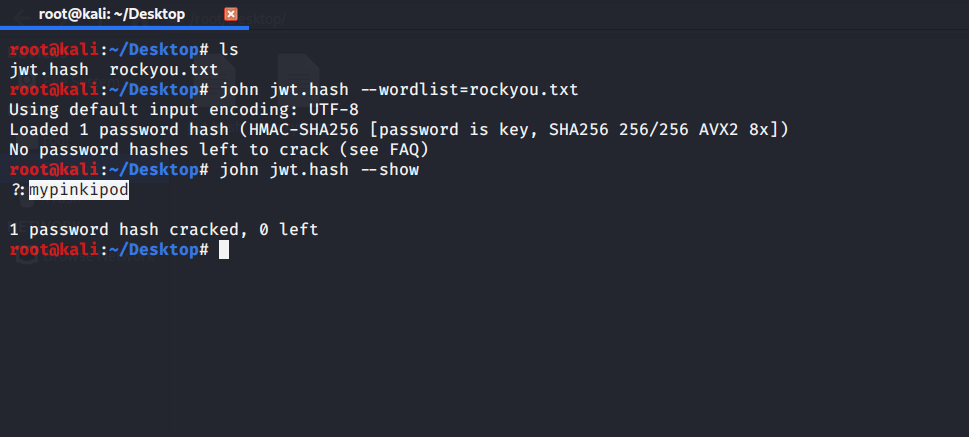
Copy the generated hash to a file for example: jwt.hash and crack it with using John the Ripper using command john jwt.hash --wordlist=rockyou.txt
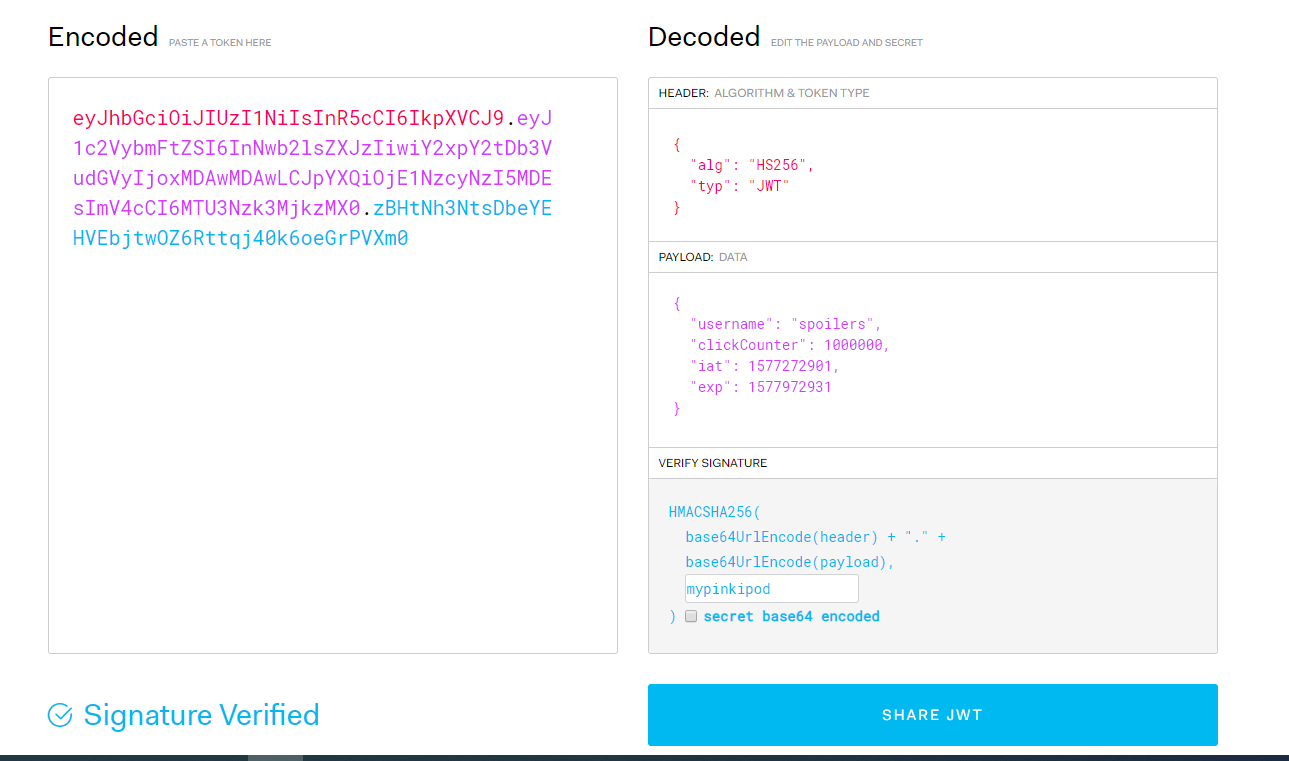
Now generate new JWT token from jwt.io using cracked secret key mypinkipod by changing clickCounter value from
0to1000000, if cookie expired change the "exp": value alsoFinally copy and paste the obtained JWT cookie from JWT.io to our challange website and refresh the page.
Voila! there is our flag..!
Misc
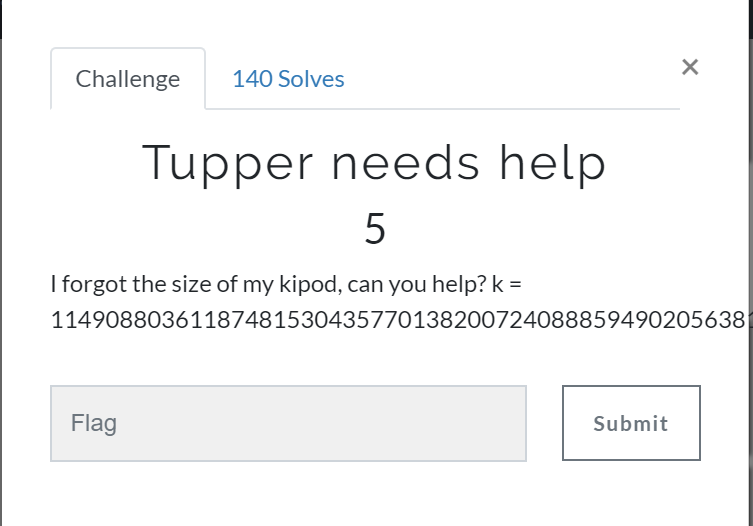
Tupper - 5
A simple challange, just goto link and Copy/Paste the K value
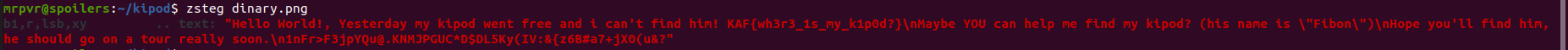
Dinary - 15
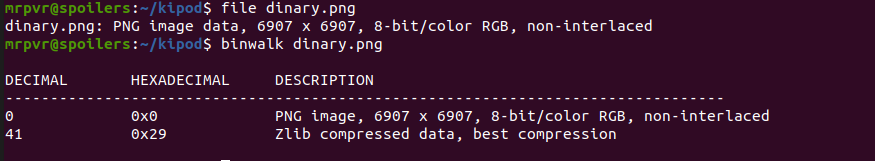
The dinary file is a valid PNG, but by analysing the png with binwalk there is some Zlib compressed data
Lets use zsteg to extract the zlib compressed data
And we got the flag !